As you know Python is a programming language usually used to build sites and software, automate tasks and conduct data analysis. It is used to create different programs plus keep in mind that it is not specialized for specific problems. It is the heart of various highly classified apps, running on servers with lots of personal data.
It is important to make sure any Python scripts you have are secure and are not leaking any personal information. Why you might ask? This is because it could lead to a data breach which has major consequences. For this reason, we have put together a list of free and useful Python code vulnerability scanning tools you can use to scan your code for potential vulnerabilities!
Why you should scan your code for Vulnerabilities?
Today we are all aware of cybersecurity threats so software developers need to know about security risks. One of the risks which are quite concerning is storing passcodes and other secrets in the source code. This could include access keys or even secret keys in plain text! You should be the least, following the basic secure coding best practices so such incidents are avoided.
Though developers know this as it is a common practice but still for those who don’t know store passwords in source code. These are usually accessed by attackers who exploit the deployment environment and pose serious risks to security. Hence why it is important to scan your code periodically for any signs of viruses, backdoors, or vulnerabilities.
The Impact of NOT keeping your code secure
The impact of having an unsecured codebase is huge. The biggest impact is a competitor or a malicious hacker gaining access to your internal infrastructure. This can result in loss of revenue, you falling behind them, trade secrets being stolen and the worst, your customers losing trust in you, ouch!
An example of a code-based attack that spread occurred back in 2016 known as Mirai Malware in which malware scanned Telnet service on Linux-based IoT boxes for hard-coded passwords which were later used in brute force attacks and compromised 400,000 devices without the knowledge of the owner.
It is a serious matter indeed which needs a lot of your attention.
5 Best Python Code Vulnerability Scanners that are free (With vulnerable code example)
#1: Bandit – Not security issue left behind
Bandit can find common security problems. For this, it processes every file and then builds a syntax tree. Against the syntax tree nodes, it then runs analyzing tools. Once it has scanned all the codes, it shall generate a report.
It was developed by the OpenStack Security Project and later moved to PyCQA. The best thing is that it can detect different security issues in Python code. It supports tests such as full-scale website code scans as it is unlimited to the .py code it can scan. It is useful for flagging issues such as internal admin pages that shouldn’t be public.
Install Bandith on Linux and Apple macOS:
- First things first, it is written in Python so it requires Python to run. If it is not installed, make sure to have it up and run before proceeding.
- For installation, you need to type the following command on the terminal
Paul@ninja-ide:~#snap install bandit
Your process of installation is going to be as follows:
Step 1: Running bandit in Python virtual environment:
Paul@nija-ide:~#Python3 –m venv bandit-env
Step 2: Finally, install bandit using Pip command:
Paul@ninja-ide:~#Pip install bandit
Use Bandit to find vulnerable code in your Python project
This is a simple process; we shall use a simple program written down in Python. The file hello_world.py file is present on the desktop.
- It would be best if you ran Bandit by using the command below:
Paul@ninja-ide:~# Bandit enter script name.py
2. It shall then scan the code and output results via the terminal.
From the command applied above you shall see the results below:
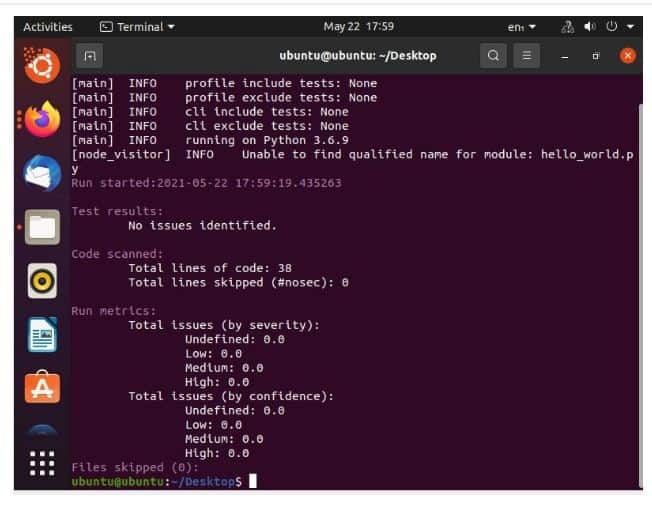
Code scanned section shall show the total number of lines scanned and also the ones that got ignored. It allows you to specify which lines of code to leave while scanning the process. This can be achieved by affixing the comment “#nosen” on the line that you intend to skip.
In the end, run metrics shall give you an overview of the entire report, as shown.
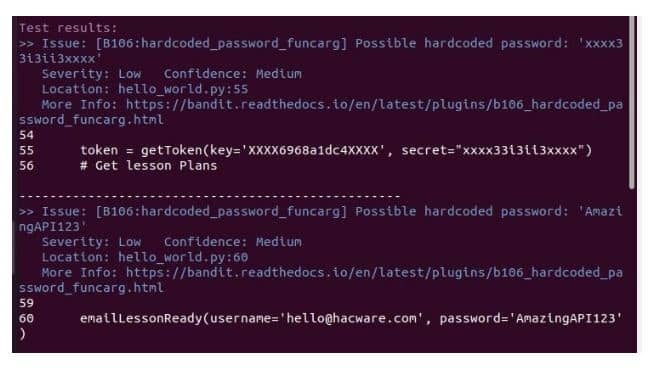
In this case, it identified two problems which in short are potential threats. both the cases came out as a result of hardcoded passcodes: One principle for secure coding is that you never need to hardcode passcodes. If we talk about developers then they mostly forget this principle.
The code however is vulnerable and can cause a serious threat. Now how can it be eliminated? You need to remove passcodes from the source code. This is the new output after we scanned the very same code with no hard-coded passcodes.
Keep another thing in your mind that Bandit did not recognize the password which is stored in the output string, it is shown below:
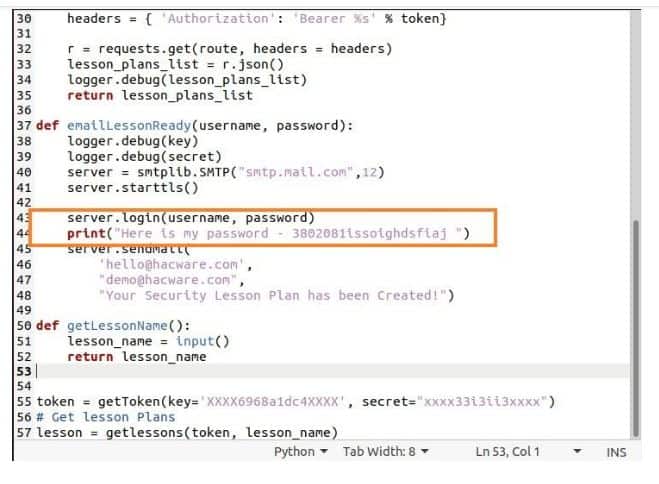
Now, if you pay more attention to the highlight or flagged parts of the script in the results, you may also find payloads that can cause harm.
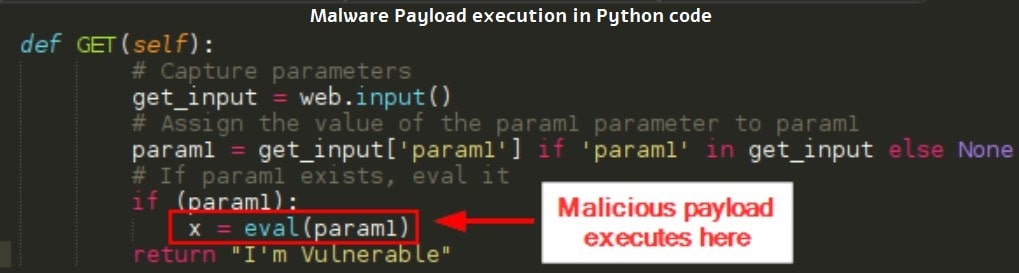
Now, keep in mind that it only recognizes problems in the actual code syntax and ignores anything which is there under comments or anything which has been saved as a string that is not treated as a password secret.
When issues identified above are eliminated it shall return no issues.
#2: Hubble
It got developed by Adobe Team. This tool comes in free and is an open-source compliance framework focused on code security. It provides alerting, reporting, on-demand profile-based auditing, and notifications with real-time security events. It reports security information to Splunk, Logstash and other endpoints.
#3: Hawkeye
This is a vulnerability, security and risk highlighting tool. Now if you want to put it into operation, you need to integrate it into continuous integration pipelines and pre-commit hooks.
This assumes that your directory structure is such that files related to package configuration are on the top level. It is open-source which means you can contribute to it or can fork it and add in new features which you want.
A Hawkeye scan could potentially reveal issues such as open ports and you leaving your FTP server open to the world.
#4: Security.py
It is a package through which you can add cookie attributes and optional security headers for different Python web frameworks.
On pip this is a package so you can install in alongside other packages easily in your Python project. Moreover, it supports all the major web frameworks such as Django, Flask, CherryPy.
#5: Salus – Security scanner and coordinator
With this, you can schedule the operation of security scanners. Run it on the repository and shall determine which scanners are required to be executed, and operated and then provide results of the entire process.
Now it includes many open-source scanner tools and uses them for its operation. This is great for CI or D pipelines which allow catching different security-related problems.
It can be configured at the repository level, for this you need to make configurations for complete projects where you can set global settings and defaults. With this, you can also generate detailed reports for analysis as well.
Solus is no longer available as it looks to be deleted from the Coinbase repository on GitHub.
Interesting Python projects with source code:
Does your security team review your code?
Vulnerability scanning comes in various shapes and sizes and code scanning is one of them. It is better that an internal red team member catches this before a hacker does and causes embarrassment. These 5 Python code vulnerability scanners will give you a good starting point so you can review the security and standards to improve. The bandit and vulnerable code example should help make the concept clear and give you an idea of what to look out in the scripts. Enjoy!