
Hacking and Penetration testing have been the hottest topics recently due to everything moving to the cloud. Ethical hacking and penetration testing skills are in high demand due to a shortage of the applications available as the requirements are significant and around 38% of employers require you to know one or some programming languages. Don’t worry as the 5 best Programming languages for Cyber Security will make sure that you are no short of what is needed to become a black-hat or white-hat hacker!
So why learn these languages in the first place? Well, cyber security is the opposite of hacking and you need to defend your data and systems. Learning languages such as Python, SQL or Java will give you the edge of having scripts and automation in place to keep your servers and network always updated and free of any security issues.
Gentle reminder: Protecting data is so serious that the fines can be very damaging to your company, recently T-mobile had to pay $2.5 Million USD for a breach that happened in 2015.
What or Who is an Ethical Hacker (or Black Hat Hacker)
This is a person who needs deep technical expertise in infosec in order to recognize potential attack vectors that give threats to both business and operational data. The ones who get employed as ethical hackers demonstrate applied knowledge that is gained through recognized industry certifications or university computer science degree programs and through practical experience working with all the security systems.
Such security thefts find security exposures in insecure system configurations and software or hardware vulnerabilities which are both known as unknown and operational weaknesses in process or technical countermeasures. Potential security threats of malicious theft include distributed denial-of-service attacks in which different computer systems are both compromised and redirected to attach a certain target, including any resource on the computing network.
The organization gives such a person-wide attitude to legitimately and repeatedly attempt to breach its computing infrastructure. This usually involves exploiting what is known as attack vectors which are used to test the resiliency of the infosec posture of the organization.
Many of the same methods and techniques are used by security thieves in order to test out IT security measures, as do their unethical counterparts, or even black hat hackers. Rather than taking advantage of vulnerabilities of personal gain, security thefts document threat intelligence in order to help the organization remediate network security via stronger infosec policies, procedures as well as technologies.
Any organization whose internet is connected to the internet or one which provides online service should consider subjecting its operating environment in order to penetrate testing which is conducted by them.
SEE ALSO: Python for Cyber Security Book and Free Course PDF Download.
What or Who is a Penetration Tester (or Pentesting)
This is a method that is used to gain assurance in IT system security by making an attempt to breach a few or all of the system’s security by using the same tools and techniques as an adversary might.
This is a method that is used to gain assurance in the organization’s vulnerability assessment and management processes, not as a primary method to identify vulnerabilities.
A penetration tester checks your company’s security policies and measures and makes sure they are working as stated. This may be trying to infect your network with viruses or malware or trying to bypass your antivirus defense.
5 Best Programming Languages for Hackers, Cyber Security and Pentesting
The cyber field is a large area with various sub-topics and professions. Here we list the 5 best programming languages that are used by hackers and cyber security professionals in 2024.
Python – Overall best Black Hat Hacker programming language

This is one of the finest programming languages, it is known among users due to being a general-purpose and high-level language that is used for security theft.
It is the best one for security thefts and is both free and open-source. It is a basic language used to help break into large databases. It has a simple syntax and is best for newbies or script kiddies. Due to its extensive libraries and packages, it is the first choice of programmers. You can also find various tutorials online to share the code from and build your own tools! Like this tutorial that shows you how to create your own Keylogger.
It is supported by a strong community that provides support to many third-party plug-ins each day. Among many features, one is interpreted feature which makes it easy to run without the need to compile. It is able to facilitate order and is easy as it is an object-oriented yet simple structured programming language.
It also provides fast reconnaissance of the host network and prototyping gets fast due to the libraries it comes with e.g. for reverse-engineering malware.
SEE ALSO: Top 11 Python Programming Language facts you MUST know as a developer.
Go Language – Top programming language for penetration testing
It is also known as Golang which got developed by Google employees, chiefly the longtime Unix guru and Google distinguished engineer Rob Pike but to be honest it is not strictly speaking a project of Google. It is developed as a community-led open-source project which is spearheaded by the leadership and has strong opinions regarding how it should be used and what direction the language should take.
It is simple to learn, straightforward, and easy for developers to read. Now, it does not have a large feature set especially when you compare it with languages such as C++ and the different C++ IDEs available. For those who do not know it is reminiscent of C in its syntax which makes it easy for longtime C developers to learn. Many of its features especially concurrency and functional programming, harken back to languages like Erlang.
Like C is used to build and maintain cross-platform enterprise apps of all kinds it has a lot in common with Java. As means of enabling quick code development which might run anywhere, you can draw a parallel between Go and Python though they have more differences than similarities.
SQL – A versatile programming language for Hackers

This is abbreviated as Structured Query Language. It is a piece of cake for all the security thefts. Now, what it does is deceive the host system and provide information to the theft.
The command it makes has a strong impact. A good yet handy tool that enters and gathers information from the corporate database, complex SQL code sequences are typed in search boxes, login boxes as well in sign-up fields. How does this help? In the extraction of required information which is hidden behind the barriers.
This is where they perform techniques such as SQL Injection and dump the databases or tables with the required information, hence why security best practices for code should be followed in your team!
Web applications which are built on the SQL server, Oracle, and MySQL are vulnerable to SQL injection attacks. What makes it the best programming language for ethical hacking is highly sensitive data exposure.
On this basis, black hat hackers are able to create as well as operate highly functioning hacking programs.
Java – Popular programing language among hackers
This is an important language for security theft without any doubt. As it has been equipped with full-stack both front-end and back-end web technologies, it makes an entry and can also alter complex systems as well. Moreover, the functions aid in flexibility in hacking websites or mobile applications and servers.
Though it can be tracked easily which is used as an advantage by professionals, sound knowledge of the language is a must. It carries robust and reliable codes.
Now, a question is asked a lot, Is Java a good language for hacking? It is in the top 5 languages for hacking and security due to being flexible with the codebase.
Use it to make the internet worms as it can manipulate browser DOM smoothly. It also allows security thefts to create mimicking attacks on the server and client side of the system.
SEE ALSO: How To Install and Upgrade Python on Kali Linux.
Bash – Best programming language for Ethical-Hackers
This one on the list is not a full-blown programming language used for security theft but it is important to have proficiency in this language. This is an open-source GNU project and in most Linux distros such as Ubuntu the default command shell.
This is a command line interpreter or you can also call it a user shell which is used to interpret user commands and deliver the output in the form of characters. It is handy while manipulating the system when you are trying to penetrate a network it shall provide automated support. There is no other programming language that can rightly fight it by modifying the file system and directory tree.
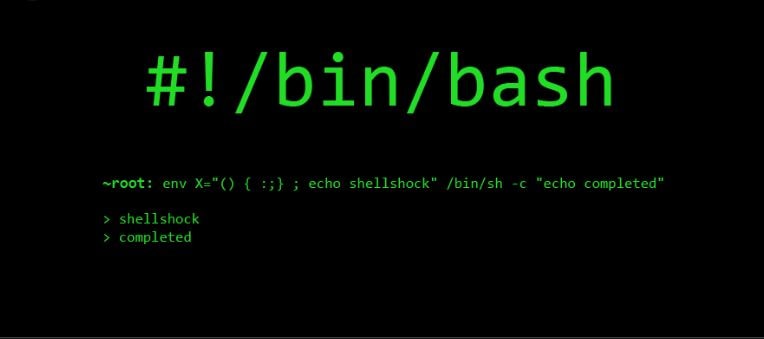
For ethical hacking tools like NMAP, aircrack-ng or Metasploit-Framework you will need knowledge of the terminal, this is because when you are using these tools, for example looking for a publically available server to hack you will need Bash knowledge to make the process quicker. Moreover, it can outperform Python when it comes to processing the startup time. It gives you a way into complex yet complicated systems with strong security. Once the access has been established it takes over and facilitates the process.
Go Vs. Python for Hacking, which to pick and why?
If we talk about Python, it is around 29+ years old but today it has a lot of popularity. It design has stood the test of time. Today both of these are seemed to be the most popular yet convenient to use programming languages.

It is a good object-oriented language but programs can also be written down in a functional programming style as well. Out of all the languages, you won’t find one which is used by more non-programmers than Python. flexibility is one of the reasons why it is so popular, use it for everything from creating APIs to enterprise-grade projects.
How does Go compare to Python in Hacking?
Python is mostly used for backend script development whereas Go is used in API-related subject areas. Hence they both are crucial but each has its own benefits over the other:
- They have a simple syntax.
- They have first-party support from all major cloud providers.
- If you are a beginner you can start with these easily.
- Easy to learn.
- Go is new when compared with Python and is designed to be fast. Go is faster than Python.
- If we talk about Python then it dominates in data science whereas Go is perfect system programming.
- Python being a senior language carries an extensive library and community built up around it.
- Dynamic typing of Python makes it better than Go for quick prototyping. This is useful as you don’t have much time when you are writing 0-day exploits or vulnerabilities.
- With Go easily run programs.
- Go was built to solve problems at a Google-sized scale making it great and ideal for working on large concurrent apps.
- Go provides support to concurrency or has the ability to run more than one program or task at the same time whereas Python does not.
Both offer unique benefits in their own ways, but there is no way you can’t and should not learn to use both.
A small but wise tip: Never stop running vulnerability scans on your network and servers. They will always show the weak link in your organization before the bad guys do. Also, you should never hack or pentest applications or servers that you do not have written permission/authorization to do so on and respect the law.
Conclusion
This article covered the top 5 best programming languages for cyber security and pentesting. All of these 5 languages including Python, Go and Java are somewhat required for cyber security and hacking-related tasks or jobs because of how widespread these languages are.
Learning these languages one by one will give you a better advantage in understanding their syntax. Hence why you should also learn about Linux, especially Kali Linux for when you go deeper into Bash territory.
FAQs about programming languages for hackers
What programming language to study for becoming a hacker?
Python, Java and Go are the most popular and useful languages you should study if you want to become an ethical hacker. This is because Python offers a vast majority of libraries that are used in cyber security. Java and Go are the foundations of most applications and web apps and having a knowledge of those two, will make pentesting a system easier for you.
What is a black hat hacker programming language?
There is no such thing as a black hat hacker programming language. Black Hat is a term used for hackers that have malicious intent to harm systems and steal data.
Which is the best programming language for cyber security?
The best programing language for cyber security is Python. This is because it currently has over 600 networking, server, reconnaissance, password-cracking and network libraries that you can start from. It also has a great community online in forums where you can ask questions and get answers from professionals with experience.
How long will It take me to learn a programing language for cyber security?
Learning a programing language is not an easy task, well depending on if you have experience it will be quicker for you. Typically it takes anywhere between 6 to 9 months until you start getting a full-grip of the language and how it integrates with cyber security.












